“Make the lie big, make it simple, keep saying it, and eventually they will believe it.”
Adolf Hitler
“In times of universal deceit, telling the truth will be a revolutionary act.”
George Orwell
It’s easy to think that you are crazy (or at least deluded) when you publish evidence of a conspiracy against a system bulging from every pocket with corruption and the treacherous means to protect it. It is even easier for people to vilify you when you challenge their protective illusions beyond credulity and then still further. Still further, yet not even close to the size of the real conspiracy being exposed by the whistleblowers Chelsea(formerly Bradley) Manning, Julian Assange and Edward Snowden. What do you consider a conspiracy? A hidden agenda? A concealed plot? When a government covers up the truth? Is it still a conspiracy when the lie is public? When they stop trying to hide what they are doing to their own people? Whatever your feelings about censorship and the cinching gauntlet of government control, sometimes people need to see this stuff for themselves.

A women delivers a speech as she stands on a chair of the public art project “Anything to Say?” at the Alexander Square in Berlin, Germany, Friday, May 1, 2015. The sculpture of the Italian artist Davide Dormino shows the whistleblowers Chelsea Manning, Julian Assange and Edward Snowden, from right, to honour their courage. (AP Photo/Michael Sohn)
Why don’t we start with WikiLeaks:
Go to this site [http://collateralmurder.com/] and try to watch the leaked videos of civilians shot in cold blood from the air in Baghdad by US helicopter gunmen. Expert training, professional military intelligence and high tech visual tools foiled by bloodlust and the ability to confuse a camera for a rocket launcher? These inept gunmen given authorization by equally inept commanders to: “Light em all up!”
And the result of this all too common and unjustified slaughter? The deaths of Reuters photographer Namir Noor-Eldeen, 22, and his assistant and driver Saeed Chmagh, 40.
One can only imagine how desperately the military doesn’t want the average citizen to see what they are sending their sons and daughters into the Army, Navy and Airforce to do. The bloodthirsty prurience of the killer as they target a victim now riddled with bullets as he crawls the bloodsoaked ground. “All you gotta do is pick up a weapon”, one soldier says over the COM as he eagerly hopes for the justification to be able to murder the already dying man.
Once you have watched the footage yourself, reading the Reuters article on the event will bring into sharper focus the forces lined up against disruption of the officially sanctioned pro-war, pro-corporate narratives. This can be clearly seen throughout the Reuters article in which reporters must repeatedly use Assange’s words to convey their own viewpoint. In other words, even Reuters must write what they think between the lines to avoid the consequences of breaking rank. A fact compounded when Reuters’ desperate attempts to find out what happened to their correspondents were met with a wall of US Military obfuscation and denials. That is until the WikiLeaks decrypting and subsequent release of the classified horrorshow. And yet we stand by and allow our governments to chase, harangue, threaten and imprison these men of courage!
And here a warning to the faint of heart, or as yet, insufficiently terrified: Watching the decrypted video causes a sickness of heart that fills the viewer to a depth that threatens any fundamental belief in the good of mankind. This gnawing malaise deepens when you take the time to view a fraction of what WikiLeaks has exposed of the war in Iraq and the US terror tactics abroad. Counterterror tactics would apply here if the video didn’t clearly show otherwise.
The image below is taken from decrypted footage exposed by wikileaks showing US soldiers torturing prisoners at Abu Ghraib.
Yet to understand the subtlety used in the widening net of damage control techniques employed as part of the surveillance and control arms of the US/UK and Canadian government one needs only look a the link posted by Reuters in their article. The video objects embedded in the page will come up blank in Google Chrome. No error, no warning, just blank. So you think the video link is broken. But check out what happens when you visit the website on the TOR network. Now suddenly you can watch the videos.
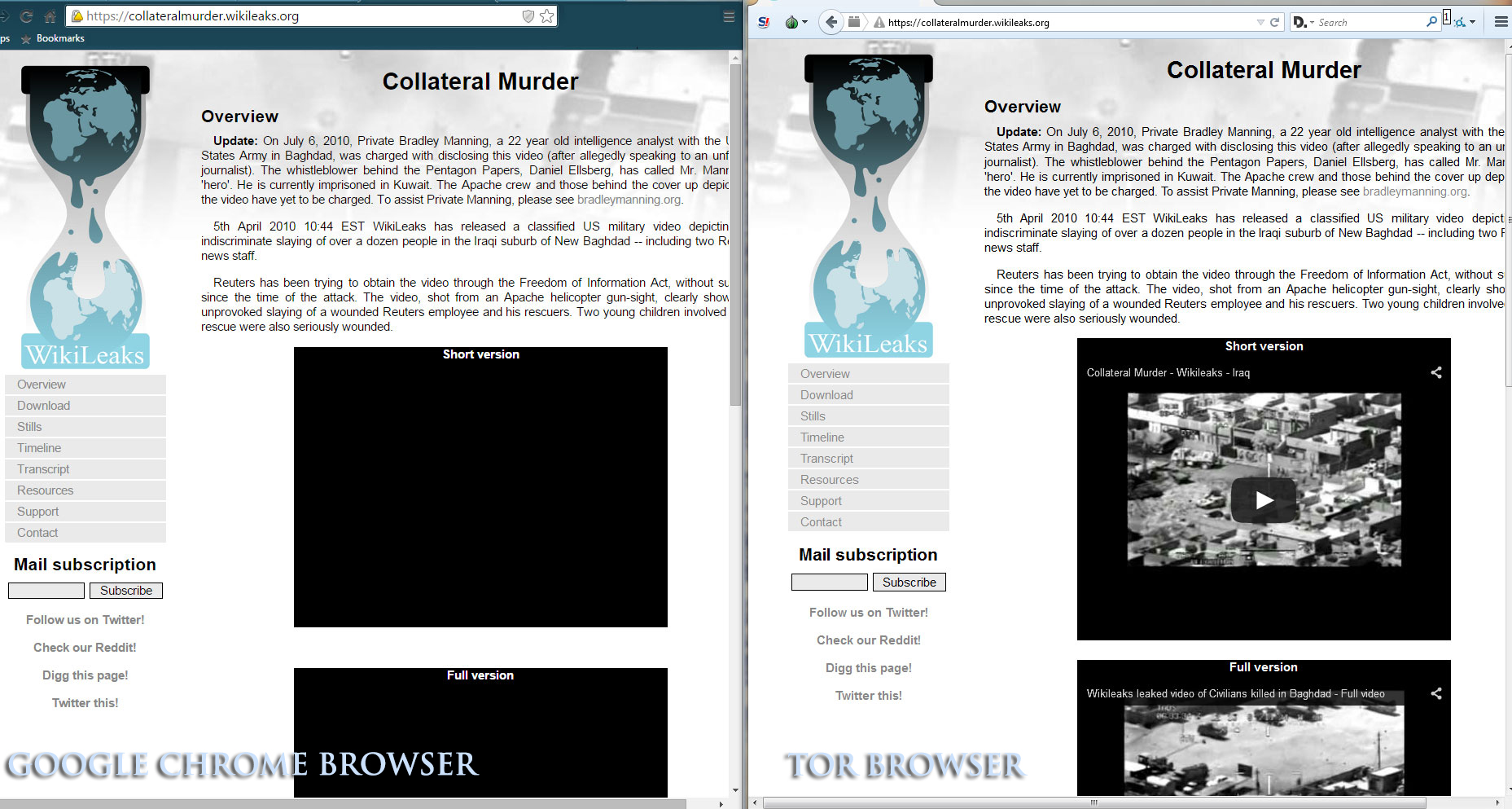
Not all government control is obvious at first. Sometimes you have to ask the ‘why’ of simple things like why videos aren’t loading.
What may not be immediately apparent in the above screenshots is that part of the authentication and site verification code in the Google Chrome browser is interacting with the collateralmurder.com website specifically! On most websites like Youtube, no login is required to watch a particular video yet here we clearly see that in the Google Chrome browser the video appears blank. To the untrained eye, the link appears to be broken. But is it? In this case the ‘blackout’ has been triggered when the Wikileaks site certificate is checked against a Verisign or Geotrust global database which is then acted upon by the browser to enable or disable certain content for being ‘dangerous’. What this implies if correct, is that Google as well as the global site verification infrastructure is complicit in censuring or ‘browning out’ information they don’t want the general public to be privy to. Now here is where it gets interesting.
If you try to watch the video directly on youtube in your TOR browser you are asked to sign in to confirm your age!
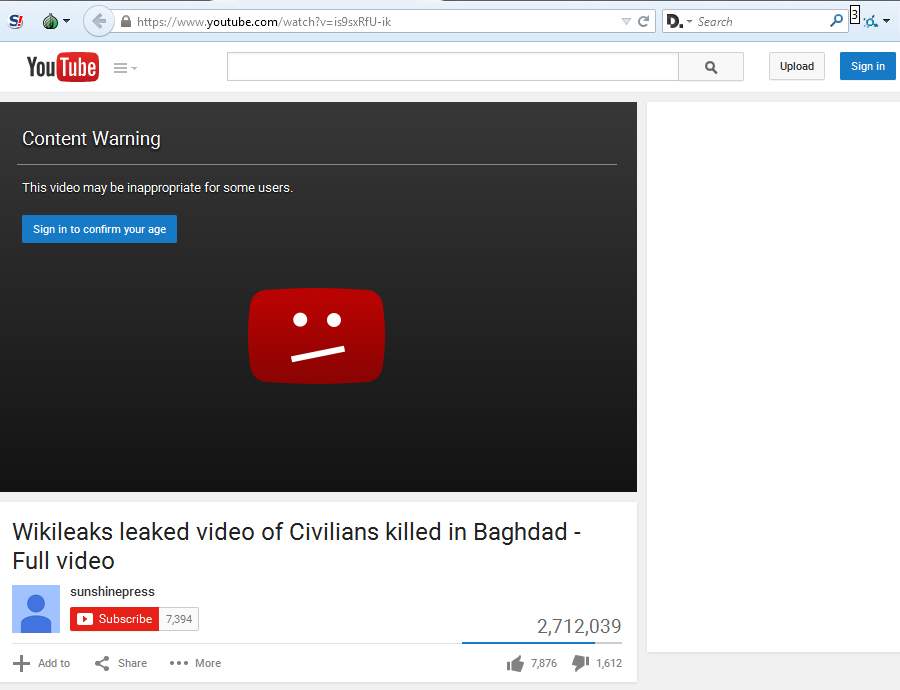 This then identifies you uniquely to the algorithmic flagging system which in turn alerts the host of watchers and controllers from the NSA, PRISM, CSIS etc. As many daily YouTube users know, this sign in is rarely required to view even the most horrendous videos. So again, this is another block put in place to track those who are viewing it while dissuading the casual observer from seeing the atrocities for themselves.
This then identifies you uniquely to the algorithmic flagging system which in turn alerts the host of watchers and controllers from the NSA, PRISM, CSIS etc. As many daily YouTube users know, this sign in is rarely required to view even the most horrendous videos. So again, this is another block put in place to track those who are viewing it while dissuading the casual observer from seeing the atrocities for themselves.
Compliance will not be enough, you will dance with a forced smile on your face like Kim Jong Un’s starving population. Remember the North Koreans could not have imagined what awaited them when Kim Il-sung came to power in 1948 after the Japanese had split the country. But now we can. History is the only map to the future worth a damn, yet it is the first thing redacted by a corrupt regime. What is happening in the US, China, Russia and elsewhere has happened before and always resulted in world war or attempts at world government.
Once conspiracy marches its jackboots with daylight impunity,
it becomes the law and is conspiracy no more!
This is all the time you will ever have to wake up and arm yourself with the means to face the truth before it is covered over like so many mass graves.
Born: December 17, 1987
Crescent, Oklahoma, U.S.
Location: 35 years in prison, reduction in rank to private (private E-1 or PVT), forfeiture of all pay and allowances,dishonorable discharge[2]

-
Chelsea Elizabeth Manning is a United States Army soldier who was convicted in July 2013 of violations of the Espionage Act and other offenses, after disclosing to WikiLeaks nearly three-quarters of a …Wikipedia
Born: 3 July 1971
Townsville, Queensland, Australia
Location:Embassy of Ecuador, London, United Kingdom(temporary asylum)
 Julian Assange (Computer programmer)
Julian Assange (Computer programmer)
-
Julian Paul Assange is an Australian computer programmer, publisher and journalist. He is known as the editor-in-chief of the website WikiLeaks, which he co-founded in 2006 after an earlier career in hacking and programming. Wikipedia
Born: June 21, 1983
Elizabeth City, North Carolina,United States
Location: Russia (temporary asylum)

-
Edward SnowdenComputer professional
-
Edward Joseph “Ed” Snowden is an American computer professional, former CIA employee, and government contractor who leaked classified information from the U.S. National Security Agency in 2013. Wikipedia
–>To use TOR all you need is a small piece of software called a Client and a specially configured browser(bundled with the client). Link1, Link2
GeoTrust was a restarted company in 2001 that acquired the security business of Equifax. The Equifax business was the basis of its fast growth. The founders of the restarted company were CEO Neal Creighton, CTO Chris Bailey and Principal Engineer Kefeng Chen. Having no previous fund raising experience Creighton, Bailey and Chen used an existing (almost bankrupt) company as the vehicle to acquire the business they had started at Equifax. The buyout of the Equifax certificate business was inexpensive given the final exit price in 2006.[1]
VeriSign acquired GeoTrust on 5 September 2006 for $125 million in cash. The main investor was St. Paul Venture Capital/VesBridge.
The pre-2001 GeoTrust was focused on the B to B exchange market which never materialized. GeoTrust became one of the few startup dotcom companies able to restart in a new direction and to achieve a successful outcome. ACG/ Mass High tech named VeriSign’s acquisition of GeoTrust as the sell side deal of the year for 2006.[2] With GeoTrust’s history, several individuals have had the title of co-founder. There are founders of the old GeoTrust which started in 1999 and had to restart in 2001 and founders of the restarted company in 2001 that sold to VeriSign in 2006 for $125 million. These may be viewed as two distinct companies with the same name in completely different businesses.[3]
Symantec acquired the GeoTrust brand in 2010 as part of its $1.28 billion acquisition of VeriSign’s security business.
Born: December 17, 1987
Crescent, Oklahoma, U.S.
Location: 35 years in prison, reduction in rank to private (private E-1 or PVT), forfeiture of all pay and allowances,dishonorable discharge[2]

-
Chelsea Elizabeth Manning is a United States Army soldier who was convicted in July 2013 of violations of the Espionage Act and other offenses, after disclosing to WikiLeaks nearly three-quarters of a …Wikipedia
Born: 3 July 1971
Townsville, Queensland, Australia
Location:Embassy of Ecuador, London, United Kingdom(temporary asylum)
 Julian Assange (Computer programmer)
Julian Assange (Computer programmer)
-
Julian Paul Assange is an Australian computer programmer, publisher and journalist. He is known as the editor-in-chief of the website WikiLeaks, which he co-founded in 2006 after an earlier career in hacking and programming. Wikipedia
Born: June 21, 1983
Elizabeth City, North Carolina,United States
Location: Russia (temporary asylum)

-
Edward SnowdenComputer professional
-
Edward Joseph “Ed” Snowden is an American computer professional, former CIA employee, and government contractor who leaked classified information from the U.S. National Security Agency in 2013. Wikipedia
–>To use TOR all you need is a small piece of software called a Client and a specially configured browser(bundled with the client). Link1, Link2
GeoTrust was a restarted company in 2001 that acquired the security business of Equifax. The Equifax business was the basis of its fast growth. The founders of the restarted company were CEO Neal Creighton, CTO Chris Bailey and Principal Engineer Kefeng Chen. Having no previous fund raising experience Creighton, Bailey and Chen used an existing (almost bankrupt) company as the vehicle to acquire the business they had started at Equifax. The buyout of the Equifax certificate business was inexpensive given the final exit price in 2006.[1]
VeriSign acquired GeoTrust on 5 September 2006 for $125 million in cash. The main investor was St. Paul Venture Capital/VesBridge.
The pre-2001 GeoTrust was focused on the B to B exchange market which never materialized. GeoTrust became one of the few startup dotcom companies able to restart in a new direction and to achieve a successful outcome. ACG/ Mass High tech named VeriSign’s acquisition of GeoTrust as the sell side deal of the year for 2006.[2] With GeoTrust’s history, several individuals have had the title of co-founder. There are founders of the old GeoTrust which started in 1999 and had to restart in 2001 and founders of the restarted company in 2001 that sold to VeriSign in 2006 for $125 million. These may be viewed as two distinct companies with the same name in completely different businesses.[3]
Symantec acquired the GeoTrust brand in 2010 as part of its $1.28 billion acquisition of VeriSign’s security business.
















